The Ultimate OpenEMR Hosting & Scaling Guide for AWS, GCP, and Enterprise Infrastructure
Are you planning to deploy OpenEMR at scale? This guide shares everything you require to host and grow OpenEMR on AWS, Google Cloud, and enterprise on-premises infrastructure. Follow this comprehensive checklist to ensure your OpenEMR is scalable, safe, and high-performing, regardless of your role: practice manager, DevOps engineer, healthcare executive, or IT administrator.
We have also covered step-by-step deployment overview on AWS and GCP, hybrid/on-premises configurations, best practices for multi-tenant design, security hardening, backup plans, database scaling, performance tuning, and cost optimization. To guarantee a successful OpenEMR implementation, refer to the numbered sections and checklists below.
1. Plan Your Deployment: Cloud vs On-Premises vs Hybrid
Evaluate your needs and choose the best hosting model before beginning installation.
Cloud Hosting
Ideal for most cases. Cloud platforms provide:
- On-demand scalability,
- Managed databases,
- Built-in backup and recovery, and
- Global availability.
As your practice expands, you can simply scale servers, databases, and storage.
Because cloud data centers provide redundancy across several availability zones, your OpenEMR can continue to operate even in the event of a facility failure.
Without requiring you to maintain actual hardware, this satisfies high uptime needs. If you are comfortable with data off-premises, desire elasticity, and require less IT management, use the cloud.
Related: How to Achieve HIPAA Compliance with OpenEMR Cloud Hosting
On-Premises Hosting
Gives you complete control over the data locality, program environment, and hardware. In areas with strict regulations, certain clinics or hospitals are required to maintain patient data on-site or inside national boundaries.
On-premises systems can range in complexity from a single physical server to a private cloud. Use on-premises if you have an established enterprise infrastructure and IT personnel, or if you have stringent data residency regulations. Keep in mind that scalability is “limited” to what your hardware can handle, and adding capacity takes time. You also take on responsibility for power, cooling, physical security, and hardware redundancy.
Hybrid Approach
Combines on-prem and cloud. Large healthcare organizations often use hybrid models, for example, running OpenEMR databases on-prem for data control, but using cloud VMs for web front-ends and backup storage. This can give a balance of compliance and scalability.
Hybrid might also be a transition strategy: gradually offloading certain components to the cloud while keeping core systems in-house.
Checklist – Planning Stage
Gather Requirements
- How many concurrent users
- Do you need support?
- What uptime is required?
- What regulatory compliance must you meet? Document these needs.
Budget Estimates
Establish your monthly operating and setup budget. On-premises has a larger initial capital expense; cloud fees increase with usage.
For comparison, an enterprise-grade solution may cost several hundred to several thousand dollars per month, depending on scale, whereas a simple AWS implementation may start at about $75 to $100 per month.
IT Expertise
Evaluate your personal knowledge. If you are unfamiliar with the cloud, it may be advisable to use AWS or GCP marketplace images or a managed service rather than beginning over.
On-premises requires Linux and network administration knowledge. If going cloud, familiarize the team with the basics of that platform’s services.
Security & Compliance
Involve your compliance officer or security team early. Start a BAA with the cloud provider.
To comply with the standards, make sure the design includes audit logging, access controls, and data encryption. If doctors will be utilizing OpenEMR remotely, consider network security.
Growth and Redundancy
Make plans for future scaling from day one. Describe how you would add a second server or a more robust database when the number of patients doubles, even if you only begin with one server. Determine your high-availability requirements. For example, can you tolerate some downtime in the event of a disaster, or do you currently require multi-zone deployment?
Once you’ve completed this preparation checklist, you’ll be able to choose the optimal deployment option. The deployment of OpenEMR on AWS, GCP, and on-premises will be discussed next.
2. Deploying OpenEMR on AWS (Amazon Web Services)
AWS is a popular choice for hosting OpenEMR due to its maturity and breadth of services.
You can deploy OpenEMR on AWS in multiple ways, from a single EC2 instance to a fully containerized, auto-scaling architecture. In this section, we’ll cover a step-by-step AWS deployment using best practices and highlight options for different scales.
Choose an AWS Deployment Method
AWS Marketplace Stacks
The OpenEMR project offers deployment-automating AWS CloudFormation templates in the AWS Marketplace.
- For instance, the OpenEMR Express stack simultaneously launches a networking configuration, an RDS MySQL database, an EC2 instance with OpenEMR, and an S3 backup bucket.
- This utilizes AWS managed services, is HIPAA-eligible, and is excellent for quick deployment.
- Pricing for the Standard tier was around $75/month for baseline AWS resources, while the Express tier can be as low as ~$10-20/month for light usage.
Manual EC2 Deployment
If you prefer a custom configuration, you can install OpenEMR on an EC2 virtual machine using a script or manually. This could require creating a LAMP stack, booting up an EC2 computer, and then installing OpenEMR. To make setup easier, you might also use Docker Compose on the EC2 instance.
A Docker Compose file, for example, allows you to run an openemr/openemr container alongside a MySQL container with persistent storage. A considerable percentage of the installation is automated using this method.
Containerized
Containerization should be considered in enterprise installations. OpenEMR can run in Docker containers on AWS ECS or EKS. This allows for advanced scalability, but it also increases complexity. EKS deployments can contain Kubernetes-managed OpenEMR pods, an Application Load Balancer for traffic, Aurora Serverless MySQL for the database, and EFS for shared file storage. Despite its complexity, this technique provides autoscaling and high availability right out of the box.
Step-by-Step: AWS EC2 Deployment (Example)
Let’s outline a common deployment path using a single EC2 + RDS (suitable for small to mid-sized setups):
Launch an EC2 Instance
In the AWS Console, launch an EC2 instance running the most recent version of Ubuntu or Amazon Linux 2. Select the type of instance. In addition to limiting access to known IP addresses or utilizing a VPN for security, ensure that the security group allows at least ports 80 and 443. Attach an elastic IP to make your server’s IP address static.
Set up the LAMP stack by installing PHP, the MySQL/MariaDB client, and Apache after SSHing into the EC2. Install additional PHP extensions. Alternatively, use Docker Compose:
version: ‘3.1’
services:
mysql:
image: mariadb:10.5
restart: always
environment:
MYSQL_ROOT_PASSWORD: <your-root-pass>
volumes:
– databasevolume:/var/lib/mysql
openemr:
image: openemr/openemr:7.0.4 # use latest OpenEMR image
restart: always
ports:
– “80:80”
– “443:443”
environment:
MYSQL_HOST: mysql
MYSQL_ROOT_PASS: <your-root-pass>
OE_USER: admin
OE_PASS: pass
volumes:
– sitevolume:/var/www/localhost/htdocs/openemr/sites
– logvolume:/var/log
depends_on:
– mysql
volumes:
databasevolume: {}
sitevolume: {}
logvolume: {}
<small>Example Docker Compose file for OpenEMR on a single EC2 VM.</small>
Use RDS for MySQL
Instead of hosting MySQL on the EC2 or in a container, you can use Amazon RDS to run MySQL or MariaDB. RDS will manage backups and updates for you.
If using RDS, create a MySQL instance. Set the OpenEMR config to point to the RDS endpoint. Ensure the RDS security group allows the EC2 instance to connect. AWS’s OpenEMR Standard architecture uses a managed MySQL database by default.
Configure Storage
OpenEMR stores uploaded files in the /openemr/sites/<sitename>/documents folder. On a single EC2, this just lives on the disk. But consider mounting durable storage.
- For example, attach a separate EBS volume to the EC2 for OpenEMR data.
- In one AWS deployment story, the admin attached a GP3 EBS volume to hold the database and sites/default files, so that if the EC2 is replaced, data remains intact on the volume.
- Mount this volume to /var/www/localhost/htdocs/openemr/sites.
- If using ECS/EKS, use EFS (Elastic File System) to provide a shared network drive that all container instances can access simultaneously.
Install OpenEMR
Download the latest OpenEMR package. Extract files into your web root. Set proper permissions.
Then run the web setup by visiting http://<your-server-ip>/openemr and follow the installer. Provide the MySQL credentials (for RDS or local DB), create an initial admin user, etc.
SSL Setup
Given healthcare data sensitivity, enable HTTPS immediately. The AWS Express stack, for example, integrates Let’s Encrypt for free SSL.
You can manually install Certbot on your EC2 to obtain a certificate for your domain. If you don’t have a domain, at least use a self-signed cert for encryption. Configure your Apache virtual host for SSL. In production, force all traffic to HTTPS.
DNS and Access
Point a DNS record to the EC2’s Elastic IP or to the ALB if using one. Verify you can access OpenEMR via the domain over HTTPS. Set up VPN or IP whitelisting if required so that only authorized networks can reach the site.
Related: OpenEMR on AWS EKS Auto Mode: A Complete Enterprise-Ready Deployment
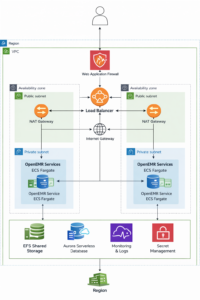
AWS Architecture Diagram
To visualize a robust AWS deployment, see the diagram below.
It shows a multi-AZ setup with containers, load balancing, and managed services that you might use for a large-scale OpenEMR deployment on AWS.
3. Deploying OpenEMR on Google Cloud Platform
Google Cloud Platform is another excellent option for hosting OpenEMR, with comparable services to AWS. GCP may appeal due to its user-friendly console and strong network performance. We’ll explore how to get OpenEMR running on GCP and highlight GCP-specific tips.
Deployment Options on GCP
Google Cloud Marketplace Image
The fastest way to deploy OpenEMR on GCP is via the Marketplace.
- A vendor offers a pre-configured OpenEMR VM image in Google Cloud Marketplace.
- With a few clicks, you can launch this image on a Google Compute Engine instance.
- The image typically includes the full LAMP stack and OpenEMR ready to configure.
- It’s a convenient starting point if you don’t want to manually install the software.
- After deployment, you should secure and tune the instance
The Marketplace route simplifies installation but still requires you to manage that VM’s OS updates and OpenEMR upgrades.
Manual VM Deployment
Similar to AWS EC2, you can create a GCE VM and install OpenEMR yourself. Provision a VM.
Choose a region close to your users and add a persistent SSD disk for good IO performance. Then follow the standard OpenEMR installation steps on that VM. You might script this with Deployment Manager or Terraform to easily repeat or adjust the setup.
Containers on GCP
For a more scalable architecture, use Google Kubernetes Engine or Cloud Run. You can containerize OpenEMR using the official Docker image and deploy it to GKE, using similar patterns as on AWS.
GKE will manage scaling and updates. If using Cloud Run, note that OpenEMR is stateful, so you’d still need Cloud SQL and a storage solution; Cloud Run alone is not typical for this workload.
Step-by-Step: Deploy via GCP Marketplace
Launch OpenEMR from Marketplace
- Log in to Google Cloud Console and find OpenEMR in the Marketplace.
- Click Launch on Compute Engine.
- You will be prompted to configure the VM, choose a machine type, disk size, and region/zone.
- The Marketplace will list the estimated cost.
- For instance, GCP’s estimate for an n1-standard-2 with 10GB SSD was around $56/month after a sustained use discount.
Configure Instance Settings
- Give your instance a name. Enable HTTP and HTTPS traffic in the VM’s firewall settings.
- You might also want to assign a static external IP. Ensure the VM is tagged or in a subnet that you can later apply firewall rules to.
Initial Login
- Once the VM is up, the vendor’s instructions will provide a way to get the OpenEMR admin password.
- Access the OpenEMR web interface via the VM’s external IP or an ephemeral URL provided.
- Complete any setup steps if required.
Secure the VM
- Immediately set up SSL.
- You can use Let’s Encrypt on this GCE VM, similar to on AWS.
- Google Cloud doesn’t have an exact equivalent of AWS ACM for VM instances, but you can obtain a cert via Certbot on the VM.
- Alternatively, put a Google Cloud HTTPS Load Balancer in front of the VM. This will terminate SSL, and you can use a free Google-managed certificate for your domain.
- In either case, ensure all OpenEMR access is over HTTPS.
- Also, configure GCP firewall rules to allow inbound HTTPS from expected sources and maybe SSH only from your IP for admin access.
Set Up Cloud SQL
The Marketplace deployment might have installed MySQL on the VM itself. If you prefer a managed database, you can migrate OpenEMR’s database to Cloud SQL for MySQL.
This involves creating a Cloud SQL instance, importing the database, and updating OpenEMR’s sqlconf.php to point to the new DB host. Cloud SQL provides automatic backups and patching. For small deployments, local MySQL is fine, but Cloud SQL helps when scaling or requiring high availability.
Storage and Backups
Implement a backup routine.
- On GCP, you can take snapshots of the persistent disk.
- Schedule daily snapshots via Cloud Scheduler + gcloud scripts or using GCP’s backup service.
- If using Cloud SQL, enable automated backups there. Additionally, export MySQL dumps to Cloud Storage daily, create a bucket, and use a cron job to dump the database and sites directory.
- You can use gsutil to copy backups to the bucket.
- Consider enabling Object Versioning on the bucket so you can retrieve older backups if needed.
- For multi-site OpenEMR deployments on GCP, remember you need to back up each site’s DB separately, similar to a single-site deployment.
Monitoring
- Enable Google Cloud’s operations suite.
- Install the monitoring and logging agents on your VM.
- This will give you dashboards for CPU, memory, and disk, and you can create uptime checks to alert if OpenEMR goes down.
- Set up log exports for audit logs if needed.
- GCP’s Identity-Aware Proxy is an option if you want to add an extra layer of authentication in front of your web UI.
4. Enterprise On-Premises and Hybrid Deployment
If you’re hosting OpenEMR on hybrid servers, this section guides enterprise-grade hybrid deployments. We’ll also discuss how to integrate with the cloud for a hybrid setup.
On-Premises Infrastructure Setup
Hardware Provisioning
Ensure you have sufficient hardware to run OpenEMR and scale.
- A typical starting point is a dedicated Linux server with at least 8 CPU cores, 16+ GB RAM, and fast SSD storage.
- For high availability, plan for at least two application servers and a clustered database.
- Common setups use VMware or Hyper-V virtualization; you might create VMs for the web server and DB server on top of physical hosts.
- Alternatively, use bare metal for maximum performance.
Operating System
Linux is the usual choice. Harden the OS by disabling unnecessary services, setting up a firewall, and ensuring regular patching. The OpenEMR wiki has a “Securing OpenEMR” page with tips like moving the OpenEMR directory to a non-web-accessible location and using Apache .htaccess to protect sensitive files. Implement these on-prem since you control the environment fully.
Database Server
For scaling on-prem, consider running MySQL/MariaDB on a separate machine from the web server. This allows you to allocate more resources to the DB and optimize it without competing with Apache/PHP. To scale further, you can implement a MySQL Cluster or Replication: e.g., a primary MySQL server handling writes and one or two replicas for read-heavy operations.
Although OpenEMR doesn’t natively split read vs write queries to different hosts, you can leverage a MySQL proxy or simply direct certain external read-only processes to replicas.
For true high availability, a multi-master cluster like Galera can be used; one community member described using a Galera cluster of 3 nodes to distribute different types of load. This is advanced and requires DB admin expertise, but it can support 1000+ concurrent users if done right.
File Storage
In an on-prem multi-server setup, use a shared storage solution for the “documents” directory and other file uploads. Options include an NFS server, a SAN-attached volume, or a distributed file system.
Ensure this storage is backed up and ideally redundant. If each OpenEMR instance is separate, you can also keep files local to each server, but then you need to sync backups across servers.
Load Balancing
For multiple application servers, put a load balancer in front.
- You can use an F5 appliance, Citrix Netscaler, or even software like HAProxy or Nginx in reverse proxy mode.
- Configure sticky sessions on the load balancer if you are not using a shared session store.
- Sticky sessions ensure a user’s requests go to the same backend server, which can be important because OpenEMR, by default, may store session data on the local filesystem or memory.
- Alternatively, configure OpenEMR to use a shared Redis or memcached server for PHP sessions, so any web node can handle requests seamlessly.
Networking and VPN
Typically, on-prem deployments are accessed over a secure corporate network or VPN. Ensure remote clinics or providers can VPN into the hospital network to use OpenEMR if needed.
Use internal DNS for the OpenEMR URL. If external access is needed, place the OpenEMR servers in a DMZ or behind a reverse proxy in the DMZ, and open only necessary ports to the outside. Consider using an SSL VPN or remote desktop gateway as an alternative to direct OpenEMR exposure.
Backups On-Prem
Leverage enterprise backup solutions like Veeam, Commvault, or Bacula to back up your VMs and databases regularly. Perform daily database dumps to an off-server location.
It’s wise to send backup copies off-site. Since on-prem hardware is prone to failures, design a Disaster Recovery plan: e.g., replicate data to a secondary data center or cloud storage, so if your primary server room has an issue, you can restore OpenEMR on standby servers elsewhere within your RTO.
Testing and Staging
In an enterprise, always maintain at least two environments: production and a staging environment. Before applying OpenEMR upgrades or patches, test them on staging with production-like data volumes. This helps avoid surprises like module incompatibilities or performance regressions in your live system.
Hybrid Considerations
Using Cloud for DR or Bursting
Even if you run OpenEMR on-prem, you can use the cloud as a backup or overflow.
- For example, you might set up an AWS environment that is normally turned off, but can be launched in case your on-prem environment goes down.
- Or use the cloud for running heavy analytics on a copy of the data, to offload from your on-prem system.
Direct Connect or VPN
If you integrate cloud resources with on-prem, set up a secure, low-latency link.
AWS Direct Connect, Azure ExpressRoute, or GCP Cloud VPN/Interconnect can link your data center to the cloud VPC privately. This avoids performance issues and ensures data is encrypted over the link.
Hybrid Identity and SSO
In an enterprise, you likely have an identity provider. Consider integrating OpenEMR login with that for single sign-on.
This might involve using something like OpenEMR’s built-in OAuth2/OpenID Connect support if available, or a SAML integration. At a minimum, manage user accounts centrally and enforce strong passwords and multi-factor authentication for remote access.
Edge Computing for Clinics
If you have remote clinics with poor internet, a hybrid idea is to deploy a local OpenEMR instance at the clinic that syncs with a central OpenEMR or central database periodically.
This is complex, but it can be done with careful planning. Most organizations will prefer a single centralized OpenEMR and invest in reliable connectivity, but this is something to consider in certain scenarios.
5. Multi-Site and Multi-Tenant Deployment Best Practices
If your goal is to host OpenEMR for multiple clinics, departments, or clients, you need to decide between a multi-site configuration or pursuing multi-tenancy. This section explains the differences and best practices for each:
Single Tenant
Out-of-the-box, each OpenEMR instance is meant for one organization. Scaling for more users in one organization is straightforward, but combining independent entities in one instance is not straightforward due to data mingling concerns.
Multi-Site Module
OpenEMR includes a Multi-Site feature, which is essentially a way to host multiple independent OpenEMR databases using a single codebase installation. In a multi-site setup, you install OpenEMR once, then use the Administration → Add New Site tool to spin up additional sites.
Each site gets its own directory under openemr/sites/ and its own database. The codebase is shared, which simplifies updates.
This is perfect for scenarios like a multi-clinic practice where each clinic’s data must be separate, or if you are an IT provider hosting OpenEMR for multiple client clinics. Best practices for multi-site:
- Plan unique site IDs or names for each site at creation.
- Automate your upgrade process: when you upgrade OpenEMR, you must run the SQL upgrade script for each site’s database. Document all the sites you host so none are forgotten during upgrades.
- Backup each site individually. The built-in backup utility will let you choose which site to back up, and restoration requires specifying the site ID. Currently, there’s no one-click “backup all sites”, so you might script a loop to back up each site’s DB and files.
- Isolate performance: Because all sites share the same code and server, one site’s heavy usage can affect others. Mitigate this by using a robust server and database server. You could even point different sites to different MySQL servers if one client is much larger.
- Security: Out of the box, sites are fairly isolated, but double-check file permissions; one site’s files should not be accessible to another. The multi-site module is designed for isolation, but ensures that user accounts exist only in their respective site database.
Multi-Tenancy
True multi-tenancy would mean a single OpenEMR instance/database holds data for multiple entities with software-enforced segregation. Important: OpenEMR is not designed for multi-tenant data separation by default. There is no simple “tenant ID” field that automatically partitions all data.
You would have to modify the application or use separate databases. If you require multi-tenancy, consider the multi-site approach. Alternatively, host multiple Docker containers or VMs, one per tenant.
That said, some larger deployments have achieved multi-tenancy with custom modifications:
- Using separate schemas within one MySQL instance for each tenant.
- Using a reverse proxy that directs users to different sites based on subdomain or URL.
- Customizing the code to enforce tenant IDs on every query, this is a significant development effort and prone to security issues if any query misses a filter.
6. Security Hardening & Compliance
Handling medical records means security is paramount. OpenEMR, being open-source, gives you the flexibility to harden the entire stack. Below is a checklist of security best practices:
Server and Network Security
Firewall and Port Control
Only expose necessary ports. For a basic deployment, this is port 443 for HTTPS. If using SSH for maintenance, don’t leave it on the default port 22 open to the world; restrict it to a jump box or VPN, or use key-based auth and IP restrictions. On cloud platforms, use Security Groups or Firewall rules; on-prem, use iptables/ufw or hardware firewalls.
Private Networking
Keep the database server off the public internet. It should be reachable only by the application server. In the cloud, place the DB in a private subnet. On-prem, don’t port-forward MySQL through the router. Similarly, if you have multiple app servers, their internal communication should be on a private network.
Web Server Config
Disable directory listings in Apache/Nginx. Use rewrite rules to block access to sensitive files. The OpenEMR wiki’s security guide suggests removing or protecting certain scripts that should not be publicly accessible. Implement those suggestions. If possible, run the web server as a low-privilege user and use Linux security modules to confine the process.
HTTPS Everywhere
Encrypt all traffic using TLS. Obtain a valid SSL/TLS certificate. Let’s Encrypt provides free certs, or use enterprise certificates. Configure your web server to redirect all HTTP to HTTPS.
Use strong cipher suites. Tools like SSL Labs can test your server. Also, encrypt data in transit between services, e.g., if using a separate DB server, enable TLS on MySQL connections too. In container setups, ensure inter-container traffic is encrypted where possible.
WAF & DDoS Protection
Consider a Web Application Firewall. Cloud users have AWS WAF or Cloud Armor, which you can configure with OWASP Core Rule Set to block common attacks.
On-prem, you might deploy a WAF appliance or software. This adds a layer of defense in case OpenEMR has an unknown vulnerability. For DDoS, cloud providers absorb most attacks; on-prem, ensure your network provider can handle or mitigate volumetric attacks.
Application Security & User Access
Strong Authentication
Enforce strong passwords for all OpenEMR user accounts.
OpenEMR allows configuring password strength policies and setting those in Administration Globals. If possible, integrate multi-factor authentication, especially for admin or remote access accounts. While OpenEMR doesn’t natively have MFA, you can front it with an SSO that does, or use VPN-based MFA.
Access Controls
Regularly review user roles and privileges in OpenEMR. Use the built-in ACL system to enforce least privilege.
- For example, a front-desk staff account should not have admin privileges.
- Use facility-specific ACLs if you have multi-site where some users should access only certain sites.
- If you have an enterprise directory, look into OpenEMR’s support for external authentication to centralize user management.
Audit Logging
Ensure that OpenEMR’s audit logging is enabled. OpenEMR can log events like logins, patient record access, etc. Aggregate these logs for analysis, e.g., send them to an ELK stack or a SIEM. HIPAA requires audit trails, so periodically review them for any odd access. Centralizing logs also helps detect if an attacker is trying to breach.
Keep Software Updated
Apply OpenEMR patches and upgrades in a timely manner. The community is active in releasing security fixes. Subscribe to OpenEMR’s announcement forum or mailing list to hear about updates. The same goes for the underlying OS and software.
Use package management and perhaps configuration management tools to keep everything up to date. Outdated software is a common entry point for attackers.
Disable Unused Features
If there are modules or services in OpenEMR you don’t use, disable them. For instance, if you’re not using the patient portal, make sure it’s turned off or not accessible. Less attack surface = better security. Similarly, remove sample data or default passwords that come with any installation.
Data Protection
Encryption at Rest
Protect PHI data at rest. On cloud, enable encryption for RDS or Cloud SQL. Encrypt EBS or persistent disks. For on-prem, use full-disk encryption for drives storing the database or documents.
That way, if a disk is stolen, the data isn’t immediately readable. OpenEMR doesn’t automatically encrypt its data within the DB, but database-level encryption or filesystem encryption provides a layer of safety.
Regular Backups & Secure Storage
As discussed in the backup section, having backups is non-negotiable.
But equally important: secure your backups. Encrypt backup files. If you dump SQL files to cloud storage, make sure that the storage bucket is locked down. Many breaches have happened because an open backup was found by malicious actors.
Retention Policies
Know how long you need to retain records. However, also have a policy for when data should be disposed of. If a tenant leaves or a clinic shuts down, and you no longer should hold their data, have a procedure to archive and securely delete data as appropriate.
Test for Vulnerabilities
Run routine vulnerability scans on your OpenEMR servers. You can use open source tools or services to scan your external IP for open ports and known vulnerabilities.
For web app security, consider using OWASP ZAP or Burp Suite on your OpenEMR URL to catch XSS or SQLi issues. Also, code scanning tools can be applied if you customize the code. Integrating a security scanner into your CI/CD is a good practice.
Incident Response
Be prepared for incidents. Have an incident response plan: if a breach is suspected, how do you isolate the system, who to contact, how to restore clean backups, and how to notify affected parties if needed. It’s better to have a plan and never need it than to scramble without one.
By following these hardening steps, you significantly reduce the risk of a security incident. Remember, security is an ongoing process; schedule regular reviews of your settings and policies. With security under control, next, we focus on safeguarding data through backups and ensuring high availability through proper planning.
7. Backup Strategies and Disaster Recovery
“Backup or bust” could be the motto for any healthcare IT system. Losing patient data is unacceptable, and downtime can disrupt care. In this section, we outline backup strategies for OpenEMR and how to architect for resilience.
Backup Essentials
Database Backups
The OpenEMR database is the most critical piece to back up, since it holds the structured medical records.
- Set up daily database dumps.
- Using mysqldump to produce an SQL file is common.
- If the data set is large, use options like single-transaction for InnoDB to avoid locking.
- Encrypt the dump file.
- Then offload it from the server, store it on another server, an external drive, or cloud storage.
- For example, one small clinic automated nightly dumps to an AWS S3 bucket for safekeeping.
- Tools like automysqlbackup or simple cron scripts can manage rotating dumps.
File Backups
Don’t forget the uploaded documents, patient images, etc., in OpenEMR’s sites directory.
These can be tarballed daily as well. If using multi-site, separate these per site. The OpenEMR admin interface has a built-in backup that packages files and the DB, but for large systems, it’s better to do it manually for more control and reliability.
Backup Frequency and Schedule
Daily full backups are a baseline. If your clinic is very busy or data is mission-critical, consider incremental backups or transaction log backups throughout the day.
- For example, enable MySQL binary logs and archive them hourly, so you could recover to any point in time.
- Ensure backups run during low-usage hours to minimize performance impact. Also, ensure backup processes are monitored.
Managed Service Backups
If using cloud DB like AWS RDS or Cloud SQL, leverage their automated backups.
RDS can take daily snapshots and keep them for X days, and you can snapshot on-demand before big changes. Still, it’s wise to export RDS/CloudSQL data to an external format periodically in case you ever need to migrate away or retrieve data outside the cloud.
Multiple Backup Locations
Follow the 3-2-1 rule: 3 copies of data, on 2 different media, 1 offsite. E.g., have the primary data, a local backup to a NAS or external disk, and an off-site backup to cloud or tape. Offsite is critical for disaster scenarios like fire or flood. Cloud storage is great for off-site if regulated data can be stored there.
Disaster Recovery Planning
Identify Potential Disasters
Ranging from hardware failure, database corruption, ransomware attacks, to natural disasters. For each, plan responses. E.g., if the main DB server crashes, do you have a failover DB ready? If the data center goes offline, do you have a backup site?
High Availability vs Backup
Know the difference: High Availability means the system stays up through certain failures. Backups mean you can restore data after a failure. Ideally, you want both. If you need near-zero downtime, invest in HA: e.g., database replication, multiple app servers behind LB. For many small providers, backups without full HA might be acceptable, with an hour or two of downtime worst-case. Larger providers should aim for HA combined with backups.
Standby Systems
If downtime tolerance is very low, maintain a warm standby system. This could be an OpenEMR instance in another region or data center that is regularly synced. In the cloud, you might have a duplicate environment in a secondary region, kept off or minimal, which can be brought online quickly. With containerization and Infrastructure as Code, you can even automate spinning up a fresh environment from backups within minutes.
Test Restores Regularly
A backup is only as good as your ability to restore it. Simulate a restoration at least quarterly.
- For example, take your latest backup and try to restore it to a test server, then boot OpenEMR and verify the data consistency.
- This tests that your backup files aren’t corrupted and that you know the restoration steps well.
- It’s common to discover a missing step during a test rather than during a real emergency.
Recovery Time and Point Objectives
Define these metrics:
Recovery Point Objective
- How much data can you afford to lose?
- If you do daily backups, worst-case, you lose <24 hours of data.
- If that’s too much, use more frequent backups or replication.
- Many clinics might be ok with one day’s data loss, but hospitals likely require near-zero data loss.
Recovery Time Objective
- How long to get back up?
- If it’s 4 hours, ensure your process can be done in that time.
- This may involve scripts to automate restoration, pre-staging backup hardware, etc.
Snapshots and Quick Recovery
In addition to backups, VM snapshots or cloud instance snapshots can drastically cut down recovery time.
- For example, if your OpenEMR VM is snapped every night, restoring that snapshot can get you a running VM quickly, and then you only need to apply transaction logs to bring to date.
- Similarly, a ZFS snapshot or LVM snapshot strategy on-prem can let you roll back in time almost instantly.
Disaster Communication
Have a plan for communicating downtime to users. If OpenEMR is down due to a disaster, clinicians should know how to switch to downtime procedures, and IT should send regular updates on restore progress. Post-incident, conduct a post-mortem to improve processes.
OpenEMR doesn’t inherently provide fancy HA or backup tools, so it’s on you as the deployer to implement these strategies. The investment in robust backups and DR is like insurance; you hope you never need it, but if you do, it can save your practice.
With backups in place, we now turn to performance and scaling considerations, particularly focusing on the database and application tuning to handle increasing loads.
8. Scaling the Database and Infrastructure
As your OpenEMR usage grows, you need to scale up the infrastructure. We’ve touched on scaling in earlier sections; here we’ll focus on database scaling, since that’s often the hardest part, and overall performance scaling strategies.
Database Scaling: Vertical vs Horizontal
OpenEMR relies on a SQL database for virtually all data. By default, the application is built to talk to a single primary database. This means traditional read/write splitting or sharding isn’t something OpenEMR handles internally. The community consensus is that vertical scaling is the first approach: use a more powerful DB server.
This might mean upgrading your cloud DB instance class or moving from 4 cores to 16 cores on your DB VM. Fortunately, MySQL can handle a lot on a single node if it’s well-tuned and on good hardware.
When vertical scaling hits limits, you consider horizontal scaling for the DB:
- Read Replicas: You can set up one or more read-only replicas of the database. OpenEMR doesn’t automatically send queries to a replica, but you can manually direct certain reporting or analytics tools to query a replica. For example, if you generate heavy monthly reports that slow the DB, run those reports on a replica database to avoid impacting the main one.
- Clustering: Solutions like Galera Cluster allow multi-master replication. In theory, you could split OpenEMR users across multiple DB nodes handling writes. However, without application awareness, this can be tricky; conflicts or deadlocks could occur if two nodes try to update the same data. If you go this route, consult a DBA and thoroughly test under load.
- Proxy & Middleware: Tools like ProxySQL or MaxScale can sit between OpenEMR and the MySQL cluster, routing queries. For example, ProxySQL could accept connections from OpenEMR and send all writes to the primary and distribute reads among replicas. But since OpenEMR’s code isn’t read-optimized, implementing a proxy might still require identifying read-heavy operations and adjusting them to benefit from replicas.
Database Performance Tuning:
Before assuming you need more DB hardware, ensure MySQL/MariaDB is tuned properly:
- InnoDB Buffer Pool: This is the primary setting to adjust for MySQL InnoDB performance. It should be set to about 70-80% of available RAM on a dedicated DB server. This allows MySQL to cache table data and indexes in memory for fast access.
- Max Connections: Increase max_connections if you expect many simultaneous users. OpenEMR may open multiple connections per user action. Ensure this is high enough to not run out during peaks, but not too high. A value of a few hundred is often sufficient; test and monitor.
- Query Optimizations: Enable the slow query log and set a threshold. Analyze the slow query log to see which queries are frequent and slow. You might find a missing index or an opportunity to add an index to a table. OpenEMR’s database is generally well-indexed, but custom forms or modules might need indexing tweaks.
- Connection Tweaks: If using a proxy or certain frameworks, ensure MySQL isn’t over-committing to client memory. For large installations, you may need to adjust thread_cache_size, table_open_cache, etc. MySQLTuner can give suggestions based on usage.
- Storage Engine Settings: InnoDB should be used for all tables. Ensure innodb_file_per_table=ON for manageability. Possibly adjust innodb_log_file_size for transaction log performance.
- Hardware for DB: Use SSDs for the DB storage. If on cloud, use provisioned IOPS volumes if you have a high query rate, to ensure low latency. Ensure low network latency between app and DB. More CPU helps complex queries or if many queries run in parallel; more RAM helps caching.
Application Layer Scaling
The application layer can be scaled by adding more instances/containers. As discussed, you might do this behind a load balancer. Key considerations:
- Use a shared file store for the /sites directory if you have multiple servers. This ensures all servers see the same documents and user-uploaded files.
- Use a shared session handler. By default, PHP might store sessions on disk. Use a database-backed PHP session or Redis/memcached so that any web server can handle any user session.
- Keep an eye on PHP-FPM or Apache process counts. High concurrency might require tuning PHP-FPM settings to utilize multiple CPUs but not exhaust them. Monitor the response times and tweak accordingly.
- If scaling beyond a couple of servers, consider an external cache. For example, use Redis to cache frequently accessed bits of data. Some advanced users implement caching for certain API calls or use something like Varnish in front of pages that can be cached. However, much of OpenEMR is dynamic, so caching opportunities are somewhat limited to things like static resources or possibly certain read-heavy data.
Handling Growth in Users and Data
- Plan for Increasing Storage: As patient records accumulate, your database grows,
- and so do file uploads. Use monitoring to project when you’ll need more disk space. It’s easier to allocate more storage proactively than in an emergency. Cloud volumes can often be expanded on the fly; on-prem use LVM or similar to allow extensions.
- Archive Old Data: Some clinics might not need instant access to very old records. OpenEMR doesn’t have a built-in archiving feature, but in theory, you could periodically offload old patient records to a data warehouse or separate database if performance becomes an issue with huge tables. This is a complex task, so only if absolutely needed.
- Optimize Client-Side Performance: As the user count grows, also ensure the front-end performance is good. OpenEMR’s UI can be heavy; enable compression on the web server, and minify assets if possible. Use a CDN for serving static content, especially if you have users in multiple geographic locations. A CDN will reduce load on your server and speed up asset delivery.
- Load Testing: Before a big go-live, conduct load tests. Simulate, say, 100 concurrent users performing typical actions. This can identify bottlenecks. Use tools like JMeter or Locust with test scripts that log into OpenEMR and perform some workflows. This is particularly important if you plan a large multi-site or a big import of data.
OpenEMR’s DB scales vertically until you must go horizontal, and any read scaling must be handled at the DB/proxy level, since the app isn’t aware of multiple DBs. Keep that in mind, often, throwing more hardware at the DB solves scaling needs up to quite high levels.
With scaling strategies sorted, we now focus on performance tuning and monitoring, which goes hand-in-hand with scaling but is slightly more focused on efficiency rather than capacity.
9. Performance Tuning and Monitoring
Ensuring OpenEMR runs smoothly and quickly is vital for user satisfaction; doctors and nurses can’t be waiting on spinning wheels during patient visits. Let’s go through tuning the application and setting up monitoring to catch performance issues early.
PHP and Application Tuning
PHP Configuration
Adjust PHP settings to accommodate OpenEMR’s workload.
- For example, increase the memory_limit to at least 256M or 512M, as loading large patient summaries or reports might require more memory.
- Increase max_execution_time to something like 120 or 300 seconds if you have scripts that run long.
- Also, adjust upload limits to allow large file uploads.
- Don’t set it too high unnecessarily, though, as it could encourage users to upload unreasonably large files.
PHP Opcode Cache
Ensure an opcode cache like OPcache is enabled. This cache compiled PHP bytecode in memory, greatly speeding up page load times by avoiding re-parsing PHP files on each request.
Verify that opcache is on and maybe increase its memory size if you have a lot of code. This is one of the easiest and most effective PHP performance boosts.
Web Server Optimization
If using Apache with mod_php, consider switching to PHP-FPM with Apache or using Nginx + PHP-FPM for potentially better resource usage. Ensure Keep-Alives are enabled.
Tune Apache’s MPM settings or PHP-FPM pool settings: e.g., set an appropriate number of child processes/threads to handle concurrent requests based on your CPU count. Too few and the server queues requests, too many and it overloads CPU or memory.
Enable GZIP Compression
Configure Apache or Nginx to compress responses using gzip.
This reduces bandwidth and speeds up load times for clients at the cost of a bit of CPU. Most modern clients support gzip encoding. Make sure not compress already compressed items. This can be as simple as a few lines in Apache config or Nginx.
Client-Side Performance
OpenEMR’s interface is largely server-generated HTML, but ensures static resources like images or JS are set with long expiry headers so browsers cache them. If you use the patient portal or any custom web components, optimize images and content there, too. Reducing front-end load will indirectly reduce server load.
Background Tasks
Schedule any heavy jobs during off-peak hours so they don’t contend with interactive users. Use nice/ionice on Linux to lower their priority.
Monitoring and Observability
Resource Monitoring
Continuously monitor server metrics: CPU usage, memory, disk I/O, network, etc.
- On-prem, you might use Nagios, Zabbix, or Grafana with Prometheus.
- In the cloud, use CloudWatch or Cloud Monitoring to set up dashboards and alarms.
- Key things to watch: DB CPU, DB memory, web server CPU, and disk latency.
Application Performance Monitoring
Consider using an APM tool to instrument OpenEMR. These can trace web requests and show which functions or SQL queries are slow. For example, you might discover a particular page always takes 5 seconds due to a specific query, then you can focus on that.
Logging
Ensure error logging is enabled in PHP. Monitor the PHP error logs for any repeated warnings or errors that could slow things down or point to misconfiguration. Also, keep an eye on MySQL logs.
Custom Health Checks
Implement a simple health check page. Use that with an uptime monitoring service or load balancer health check. This way, if OpenEMR becomes unresponsive, you get alerted immediately.
Cloud-managed setups on AWS EKS had an optional Prometheus/Grafana stack for deep metrics and alerts. Even if you don’t replicate that fully, try to incorporate parts of it. For instance, run a Prometheus node exporter on your VMs to gather system metrics, and Grafana to visualize them.
User Experience Monitoring
Pay attention to user feedback; if staff say “the system is slow at 4 pm every day”, correlate that with what’s happening. Use browser-based monitoring for front-end performance if needed.
Scaling Triggers
Set up monitoring-based triggers for scaling. For example, if CPU > 70% for 5 minutes, add another app server instance. Or if DB CPU > 80%, send an alert to consider scaling up. On a Kubernetes cluster, use the Horizontal Pod Autoscaler to add pods when needed.
Capacity Planning
Regularly review logs to see growth trends. If the number of patient records is growing 10% every month, ensure you project at what point the current DB size or server size might be insufficient. Plan upgrades ahead of time rather than after slowness has already impacted users.
Performance Troubleshooting Tips
- If the system is suddenly slow, check for any recent changes. Often, performance issues tie back to an update or a new integration pulling data.
- Check for database locks; a long-running query can lock a table and cause others to wait. Tools like SHOW PROCESSLIST in MySQL or performance_schema can reveal if threads are stuck waiting.
- Verify that your backups or maintenance jobs aren’t running during business hours, as they can hog DB or IO resources.
- If using virtualization, ensure the host isn’t overcommitted. For example, if running OpenEMR VM on a host that also runs other heavy VMs, you could be contending for physical resources.
- Use the EXPLAIN statement on slow SQL queries to see if they are using indexes. Add indexes if needed.
- Clean up database bloat: Over time, certain tables might grow huge.
- Archiving or truncating old log entries can improve performance.
- Optimize your web server configuration for concurrency, e.g., in Apache, use the Event MPM for better performance under load, or in PHP-FPM, use on-demand process management to free up PHP workers when idle.
Monitoring is your early warning system. Many catastrophic failures or slowdowns give warning signs. By staying on top of these metrics, you can intervene before it impacts the clinicians using the system.
Finally, after making the system fast and reliable, you want to ensure it doesn’t break the bank. In the next section, we’ll cover cost optimization strategies so you get the most value from your OpenEMR infrastructure.
10. Cost Optimization Strategies
Running OpenEMR efficiently isn’t just about tech; it’s also about controlling costs, especially in cloud environments where resources = money. Here are some tips to optimize costs without sacrificing performance or reliability:
Right-Size Your Instances
One of the easiest wins is to ensure each server is the appropriate size.
- Cloud providers have many instance types; choose one that matches your actual usage patterns.
- If your CPU usage sits at 10% on an 8-core machine, you can probably scale down to 4 cores.
- Conversely, if you’re pegging a small instance at 100%, a slightly larger instance might handle the load more efficiently without significantly higher cost if it prevents slowdowns.
- Use monitoring data to adjust sizes periodically.
Use Auto-Scaling
In AWS or GCP, leverage auto-scaling for the web tier. This means during low usage, you might run only 1 server, but during peaks, you run 3. This automatic scaling up and down ensures you pay only for needed capacity. Similarly, for databases, if using Aurora Serverless or Cloud SQL with autoscaling, the DB can scale down at night to save cost, then ramp up for daytime load.
Turn Off Unused Resources
If you have dev/test environments, shut them down when not in use. On-prem, this saves power and hardware strain; in the cloud, this stops billing for compute. Use automation to spin up test environments on-demand.
Spot/Preemptible Instances for Non-Prod
For training or testing servers, consider using AWS Spot instances or GCP Preemptible VMs, which are much cheaper, though they can be terminated if capacity is needed. This is not for production, but great for batch processing or QA environments that can tolerate restarts.
Optimize Storage Costs
Use the appropriate storage type. In AWS, for instance, if you don’t need high IOPS on an EBS volume, use General Purpose, which is cheaper than provisioned IOPS.
- For file storage, S3 is cheaper than EBS; maybe older documents can be offloaded to S3 and accessed via a link rather than kept on expensive disk.
- In GCP, Standard vs Nearline vs Coldline storage: you could archive old backups to colder tiers to save money. Just watch the retrieval costs.
Review and Prune Backups
Speaking of backups, storing dozens of full backups indefinitely can get costly.
- Implement a retention policy: e.g., keep daily backups for 7 days, weekly for 4 weeks, monthly for 6 months, etc.
- Delete older ones beyond that. Automated lifecycle rules in S3 or Cloud Storage can transition or delete objects after a certain time.
Reserved/Committed Discounts
If you’re confident about your baseline usage, buy reserved instances or committed use.
- For example, if you know you’ll run a DB server continuously, a 3-year reserved instance could save ~30-60% compared to on-demand pricing.
- Just be careful not over-commit.
- Often, getting a reserved DB and keeping auto-scaling on for the front-ends is a good balance.
Use Free & Open Source Tools
This is more about not spending on proprietary solutions unnecessarily.
- OpenEMR itself is open source.
- Use open-source databases.
- For monitoring, use open-source stacks like ELK or Prometheus instead of costly monitoring services, if the budget is tight.
- If you need integrations, see if open standards like FHIR can be used before considering expensive interface engines.
Avoid Over-Engineering for Small Deployments
One pitfall is to copy an enterprise architecture for a small clinic. That can lead to paying for a lot of infrastructure that’s rarely used. As one engineer noted, for a tiny clinic, having separate servers for web and DB, plus load balancers and multi-AZ, “offered no real benefit” and just raised costs.
In that case, a single properly sized instance was enough and far cheaper. Always tailor the architecture to the scale: start simple, and only add complexity (and cost) when necessary for capacity or reliability.
Monitor Cloud Bills
Enable billing alerts. Both AWS and GCP let you set thresholds or get reports. If a cost spikes, investigate immediately; it could be an inefficiency. Use cost analysis tools to see which services cost the most.
Optimize Database Costs
In AWS, for example, Aurora Serverless v2 was mentioned as charging per second of usage, this can be cost-effective if your load is sporadic. If your load is steady and high, a provisioned standard RDS might be cheaper. Know your usage pattern and pick the right billing model. Also, clean up unused data to keep storage costs down.
Network Egress
Cloud providers charge for data going out to the internet.
- If your OpenEMR is used by many remote users, this can add up.
- Mitigate by keeping things efficient.
- For an on-prem to cloud hybrid, consider a direct connection if data transfer is high, as it might be cheaper per GB.
- For user access, perhaps encourage the use of a central terminal server or something to limit massive data egress.
By applying these cost-saving strategies, you can often run OpenEMR at a fraction of the cost of proprietary EHR systems.
- For instance, one reference architecture touted an enterprise-grade OpenEMR on AWS at ~$320/month for typical use, scaling far beyond a single practice’s needs but still reasonable compared to commercial EHR hosting.
- If you implement only what you need and keep resources optimized, OpenEMR truly lives up to its promise of a low-cost solution.
Now that we’ve covered technology angles from deployment through optimization, let’s recap pitfalls to avoid and conclude the guide.
Related: Why Your OpenEMR AWS Bill Is Higher Than Expected (and How to Fix It)
11. Common Pitfalls to Avoid
In deploying and scaling OpenEMR, certain mistakes often come up often. Here are common pitfalls and how to avoid them:
Skipping Backups Until It’s Too Late
It’s easy to set up a system and forget to implement backups until a crash or data loss happens.
- Set up backups from day one.
- Even during testing, have a backup routine. And remember to test restore procedures.
- Nothing is worse than thinking you have backups, then finding they don’t work when needed.
Not Encrypting PHI Data
Running OpenEMR on HTTP or storing databases on unencrypted disks is risky and likely non-compliant.
- Always use HTTPS, and enable encryption at rest. Double-check that backups are encrypted too.
- This ensures patient data isn’t exposed if someone intercepts traffic or steals a drive.
Underestimating Resource Needs
A common issue is choosing too small a server or not allocating enough memory to MySQL, leading to poor performance and crashes.
- Follow recommended specs (e.g., at least 8GB RAM for production, SSD storage, etc.).
- Monitor the system; if it’s struggling, don’t wait for users to scream, scale it up. It’s better to have a bit of headroom.
Overestimating Resource Needs
The flip side is spending too much on a complex setup that you don’t actually utilize. For instance, using a multi-region, containerized setup for a small single-clinic deployment is overkill and wastes money and administration effort.
- Start with a simple architecture, and prove the need for each component as you add it.
- As one case study found, a single EC2 with Docker was perfectly fine for a small practice and much cheaper than a multi-tier design.
Neglecting Updates and Patches
An OpenEMR instance left untouched for years will accrue security vulnerabilities and likely performance issues.
- Keep a maintenance schedule.
- Plan to apply OpenEMR patch releases or upgrades at least once or twice a year.
- Same for the OS and other software.
- If you fell far behind, allocate time to catch up; don’t stay on an old version that might have known security holes.
Poor Multi-Tenancy Implementation
Trying to jam multiple clinics into one OpenEMR database without proper isolation can lead to privacy breaches or just management nightmares.
- Use the multi-site feature or separate instances for multi-tenancy.
- If you absolutely attempt code-level multi-tenancy, extensively test that data never crosses over, and weigh if the complexity is worth it vs. simply running multiple OpenEMR instances.
No Load Testing or Capacity Planning
Assuming “it will scale” without testing is risky. Some have hit performance walls when adding more clinics or users, and then had to scramble to re-architect.
- Before adding a major load, do a test migration or load test.
- Monitor how the system behaves and upgrade the infrastructure proactively.
- Also, periodically review growth trends.
Ignoring “Noisy Neighbor” Issues
In multi-site or multi-tenant setups, one tenant could hog resources and degrade service for others.
- Implement monitoring per site, and use resource limits or at least move a heavy tenant to a dedicated server if needed.
- Communication with clients is key, too. If one clinic plans a massive data import, you might schedule it during off-hours so it doesn’t affect others.
Weak Security Practices for Admin Access
Using default passwords, sharing accounts among staff, or accessing the server over unsecured channels can lead to breaches.
- Enforce unique user accounts, strong passwords, and MFA for admin users.
- Never use “admin/pass” in production.
- Use SSH keys for server access, and preferably access servers only over VPN or secure jump boxes.
Not Having a Disaster Plan
Backups are part of it, but many forget the process of recovery. Who does what when systems go down? Without planning, recovery is slower and more chaotic.
- Write a simple disaster recovery plan.
- Include steps for common scenarios.
- Assign roles, who is responsible for initiating the restore, who communicates to the staff, etc.
- Practice it via drills.
Avoiding these pitfalls comes down to foresight and discipline: assume things will go wrong at some point and set up defenses in advance. It’s far easier to address issues on your terms than in a crisis.
CapMinds OpenEMR Hosting & Scaling Service
If you’re turning this guide into a real-world deployment, CapMinds helps you operationalize OpenEMR at scale, without the typical “works in dev, breaks in production” curve.
We deliver end-to-end cloud infrastructure engineering, security hardening, and performance programs designed specifically for healthcare workloads across AWS, GCP, and other cloud environments.
Our OpenEMR Hosting & Scaling Service scope typically includes:
- Cloud architecture & migration services
- Containerization & orchestration services
- Database scaling & tuning services
- Security & compliance services
- Backup, disaster recovery & business continuity services
- Observability & SRE services
- Cost optimization services
Whether you’re scaling a single clinic, a multi-site network, or a hosted multi-tenant model, CapMinds can design, deploy, and run your OpenEMR infrastructure, and more, with the rigor healthcare systems expect.